Introduction
Understanding the intricacies of HIPAA compliance is crucial for any healthcare-related organization. Ensuring the privacy and security of patient health information is not only a legal obligation but also a cornerstone of patient trust and the integrity of your practice. This comprehensive guide outlines the steps to achieve and maintain HIPAA compliance, focusing on safeguarding sensitive health information.
Key Takeaways
– The Health Insurance Portability and Accountability Act (HIPAA) mandates national standards to protect patient health information, encompassing privacy, security, and breach notification rules.
– Compliance requires implementing a combination of technical, administrative, and physical safeguards, alongside regular risk assessments and management of electronic protected health information (e-PHI).
– Staying HIPAA compliant is a continuous process that involves updating compliance plans, training staff, monitoring systems, and adapting to new technologies such as cloud computing.

Understanding HIPAA Compliance
HIPAA compliance is a vital aspect of modern healthcare, ensuring that patient information remains confidential and secure in the digital age. The Health Insurance Portability and Accountability Act (HIPAA) establishes national standards to prevent the unauthorized sharing of health information, thereby protecting patient privacy.
HIPAA affects not only healthcare providers but also insurers and business associates involved in handling patient data. By adhering to these regulations, healthcare entities reinforce the trust of their patients and uphold the integrity of their operations.
Key Components of HIPAA Compliance
HIPAA compliance is built on three key rules:
-
The Privacy Rule: Protects the confidentiality of patient health records.
-
The Security Rule: Safeguards electronic versions of patient health information.
-
The Breach Notification Rule: Outlines steps to follow if patient data is compromised.
We will explore each of these rules in detail, providing actionable insights to help you meet HIPAA standards.
Privacy Rule
The HIPAA Privacy Rule sets the standards for protecting personal health information. It applies to all forms of patient data, whether electronic, written, or oral. The rule allows patients to access and amend their health records, while also placing limits on the use and disclosure of such information without patient consent.
This rule ensures that patient information is handled with care and confidentiality, supporting both individual privacy rights and the broader goals of public health and quality healthcare.
Security Rule
In an era where cyber threats are prevalent, the HIPAA Security Rule is crucial for protecting electronic protected health information (e-PHI). This rule provides a flexible framework that allows healthcare organizations to implement security measures tailored to their specific needs and capabilities.
Key security measures include:
– Access Controls: Restricting access to authorized individuals.
– Unique User Identifiers: Assigning unique IDs to track access and usage.
– Audit Controls: Monitoring and recording activities related to e-PHI.
– Encryption: Protecting data during transmission and storage.
– Authentication: Verifying the identity of individuals accessing e-PHI.
These measures collectively enhance the security of e-PHI, preventing unauthorized access and ensuring data integrity.

Breach Notification Rule
The HIPAA Breach Notification Rule mandates prompt reporting of data breaches involving protected health information. Covered entities and their business associates must notify affected individuals, the Department of Health and Human Services, and in certain cases, the media.
Key elements of the rule include:
– Transparency: Informing affected individuals about breaches.
– Accountability: Holding responsible parties accountable for breaches.
– Timeliness: Prompt notification to mitigate potential harm.
– Encryption: Using encryption to render data unreadable to unauthorized parties.
By following these guidelines, healthcare organizations can maintain trust and take swift action to address breaches.
Implementing Technical Safeguards
Technical safeguards are essential for protecting e-PHI. They include:
– Access Controls: Ensuring only authorized personnel can access sensitive data.
– Encryption: Protecting data during transmission and storage.
– Audit Controls: Tracking access and modifications to e-PHI.
– Authentication: Verifying user identities before granting access.
– Transmission Security: Securing data during electronic transmission.
These safeguards create a robust defense against cyber threats, ensuring the confidentiality and integrity of patient data.
Implementing Administrative Safeguards
Administrative safeguards provide a framework for managing and protecting e-PHI. Key components include:
– Security Management Process: Conducting risk assessments and implementing security measures.
– Security Personnel: Designating a security official responsible for HIPAA compliance.
– Workforce Training: Educating employees about HIPAA policies and procedures.
– Information Access Management: Controlling access to e-PHI based on roles and responsibilities.
– Contingency Planning: Preparing for emergencies that could affect e-PHI.
These measures ensure that staff understand and adhere to HIPAA regulations, reducing the risk of breaches.
Implementing Physical Safeguards
Physical safeguards protect the physical environment where e-PHI is stored. They include:
– Facility Access Controls: Limiting access to areas where e-PHI is stored.
– Workstation Use: Implementing policies for secure workstation use.
– Device and Media Controls: Managing the disposal and reuse of devices and media containing e-PHI.
– Physical Security: Using locks, alarms, and surveillance to secure facilities.
These safeguards prevent unauthorized physical access to patient data, complementing technical and administrative measures.
Role of Business Associates
Business associates play a critical role in HIPAA compliance. These are entities that handle e-PHI on behalf of covered entities. They must:
– Enter into Business Associate Agreements (BAAs): Legal agreements outlining their responsibilities.
– Implement Safeguards: Protect e-PHI as mandated by HIPAA.
– Report Breaches: Notify covered entities of any breaches promptly.
By ensuring that business associates comply with HIPAA, covered entities can extend their security practices across the entire network of partners.
Achieving HIPAA Compliance in the Cloud
Cloud computing offers many benefits, but it also presents unique challenges for HIPAA compliance. Healthcare organizations must:
– Choose the Right Provider: Select cloud service providers that comply with HIPAA standards.
– Implement Security Measures: Use encryption, access controls, and audit logs to protect e-PHI in the cloud.
– Monitor Compliance: Regularly review and update cloud security practices.
Selecting a cloud service provider involves thorough evaluation and establishing a Business Associate Agreement to ensure they meet HIPAA requirements.
Preparing for HIPAA Audits and Investigations
Healthcare organizations must be prepared for HIPAA audits, which can include desk reviews and onsite inspections. Key preparation steps include:
– Documentation: Maintaining accurate records of compliance efforts.
– Risk Assessments: Regularly evaluating security risks and implementing necessary measures.
– Training: Ensuring staff are knowledgeable about HIPAA requirements.
– Security Reviews: Conducting regular reviews of physical and digital security measures.
Being audit-ready demonstrates a commitment to protecting patient information and complying with HIPAA.
Maintaining Ongoing HIPAA Compliance
HIPAA compliance is an ongoing effort. Organizations must continuously:
– Update Policies: Regularly revise compliance plans to reflect changes in technology and regulations.
– Train Staff: Provide continuous education on HIPAA requirements.
– Monitor Systems: Keep a vigilant watch over security systems to identify and address vulnerabilities.
A proactive approach to HIPAA compliance ensures the highest standards of data security and patient privacy.

Summary
Navigating the complexities of HIPAA compliance is essential for protecting patient health information. By implementing robust privacy, security, and breach notification measures, healthcare organizations can uphold the trust of their patients and ensure the integrity of their operations. This guide serves as a roadmap to achieving and maintaining HIPAA compliance, reflecting Aayan India’s commitment to delivering secure and reliable IT solutions for the healthcare industry.
Frequently Asked Questions
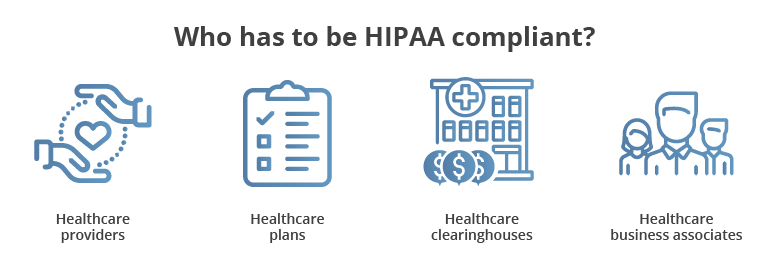
What entities are required to comply with HIPAA regulations?
Entities such as healthcare providers, health plans, healthcare clearinghouses, and business associates that handle health information must comply with HIPAA regulations to protect sensitive health information.
How does the HIPAA Privacy Rule protect patient information?
The Privacy Rule establishes national standards for handling and sharing health information, giving patients the right to access and amend their records while limiting unauthorized disclosures.
What are some examples of technical safeguards required by the HIPAA Security Rule?
Examples include access controls, unique user identifiers, encryption, audit controls, and transmission security protocols to protect e-PHI from unauthorized access and ensure its integrity.
What is the role of a Business Associate Agreement (BAA) in HIPAA compliance?
A BAA is a legally binding agreement that outlines the responsibilities of business associates in protecting e-PHI and maintaining HIPAA compliance through safeguards and breach notification protocols.
How can healthcare organizations prepare for a HIPAA audit?
Organizations can prepare by maintaining accurate documentation, regularly assessing IT security risks, conducting physical security reviews, and ensuring staff are well-trained in HIPAA standards.